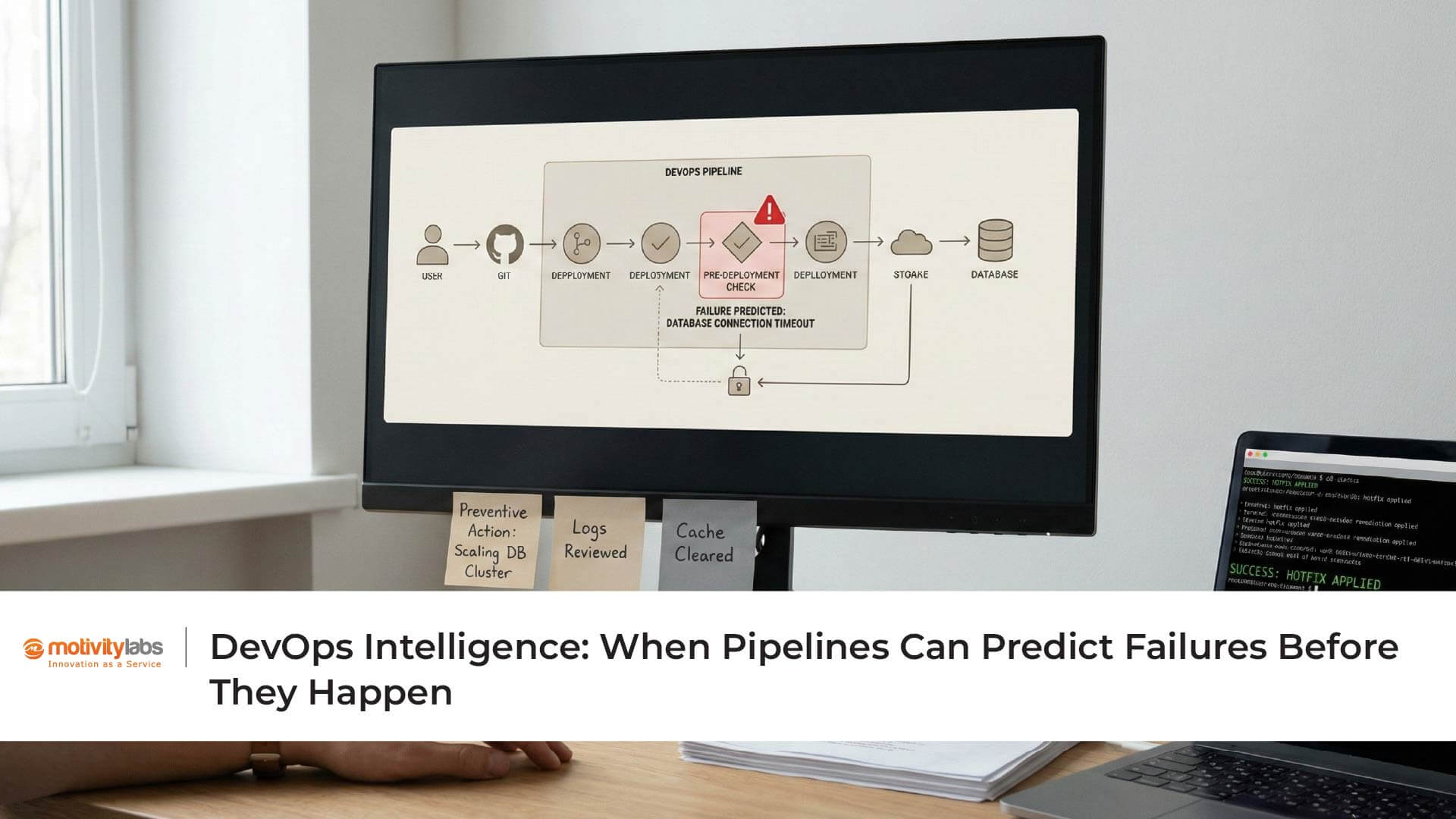
In many instances, data being in flight or at rest often gets ignored or left unencrypted. Also many times, organizations put away role-oriented security to allow faster production. This section focuses on various critical issues associated with Prioritize Security in DevOps to understand potential linked vulnerabilities and ways to resolve them.
Security in DevOps – Prioritizing It
Enterprises across the globe, for the last two decades, have visualized security as just another add-on in DevOps. However, in order to ensure the right level of protection for applications, the security technologies and approaches must be systematic to the applications and data produced by them. Security within DevOps is required to be an integrated part of its different automated steps as an enterprise moves from the stage of development and testing to the final stage of operations.
Organizations are required to adopt the new concept of “continuous security”, which means that they need to Prioritize Security in DevOps, not only during the production phase but during all phases of application development. Identity access management (IAM) is another critical area to focus on with respect to DevOps and production systems.
Search for Vulnerabilities
Detecting security vulnerabilities at the time of running the DevOps automation process is quite an essential process.
Enterprises are required to search for answers to the following questions:
- Has an enterprise provided developers with the proper rights to access the application data and code?
- Has an enterprise ensured that all copies of the application data, application code, and the application itself produced during the DevOps process have been tracked and maintained with the same level of security?
- Have enterprises tracked down identities at a fine-grained level, including data storage objects and microservices?
- Have enterprises made security centralized in order to track different components of production and DevOps using the same repository or database?
Many tech experts believe that DevOps should limit its security level to grand developers with the freedom to develop and deploy software in a real quick time. But if the goal of an enterprise is DevOps to provide true speed-to-market and agility by automating numerous development activities, then an enterprise should automate its DevOps security.
Invest Wisely in Security Solutions
DevOps production servers incorporate more heterogeneous and distributed systems, and thus, demand enterprises to invest in efficient security solutions such as identity access management (IAM). Such security solutions
- Deliver common identity validation for different systems of the DevOps process.
- Identify, neutralize, and resolve system security issues automatically and centrally.
- Deliver IAM services to the data object layers and microservices.
The use of IAM within production and DevOps is reflecting impressive growth as enterprises are modernizing their technologies and security approaches in order to align with the use of DevOps and the public cloud.
DevOps Security – Putting It to Test
After an enterprise ensures the implementation of an advanced security system that can manage its technologies and DevOps systems, they are faced with the task to ensure that the security system is working correctly.
The assurance can be done either by auditing or conducting penetration testing on the production and DevOps systems. Conducting penetration testing on DevOps tools and servers is a little tricky as compared to conducting on data storage and production application as it requires simulating attacks on different targets.
Play It Smartly
Formulating a robust strategy for DevOps security is more about processes and people, and less about technology. Enterprise can play a smart game by
Equipping their developers with the required knowledge to become security-alert. It encourages them to manage security systems in a well-thought and well-planned manner.
Ensuring that their developers have the required tools to create secure systems, and maintain the desired security level of their DevOps systems. They must also ensure that security technology as well as security approaches are restricted to identity-based systems covering most of the system under management.
Setting up metrics and monitoring systems to analyze the net effect of their Prioritize Security in DevOps. They can do that by proactively identifying threats and responding accordingly.
Testing their security at regular intervals to ensure its continued effectiveness.
Developers Hold the Key
Moving forward, organizations will be required to work in close coordination with developers as they are gradually becoming the center point to address numerous security issues. Both in DevOps systems and production, developers possess the most power to fix security threats. Continuous support from the IT leadership mixed with great training can ensure that developers are fully trained to do their job. The need to invest in DevOps technology and training has become stronger than ever.
To know more or to talk to our expert write to us today: marketing@motivitylabs.com